dark.fail hacked [UPDATED]
UPDATE. Is dark.fail down? No, but after the hack and seizing dark.fail domain – dark.fail moved to DARK.PE
Hackers seized control of a dark web market directory to steal Bitcoin from customers who attempted to buy drugs as usual. The attackers used a rather common phishing technique and managed to succeed thanks to an exceptionally high level of professionalism. The Vice online magazine was the first to report this news.
The name of that ill-fated web resource is dark.fail. For four whole days, hackers were using the opportunity to steal crypto and confidential information of people who visited any of the markets linked by the directory.
What Exactly Happened?
On April 28, someone acquired dark.fail. This person never revealed their name. To transfer the site’s ownership to a new administrator, the perpetrators relied on fake court orders.
Dark.fail is managed by privacy-centric Njalla, co-founded by Pirate Bay’s Peter Sunde in 2017. This service acts as middleware for individuals who would like to purchase domains anonymously. It bought dark.fail from Tucows, via Tucows’ Hover.
Sunde took to Twitter to explain how the story unfolded. The district court of Cologne, Germany allegedly sent an order to Tucows to demand ownership of three domains. One of them was registered through Hover and the others with Njalla.
Hover promptly transferred dark.fail to the hacker’s Namecheap registration. Sunde emphasized that the forged order also featured a gag order, which means the registrant didn’t know what was going on.
This story might sound a bit weird — but we should take into account that Tucows might need to deal with a whole avalanche of court orders. Maybe, they were just too busy to scrutinize one particular paper. Meanwhile, it was a classic phishing trick. The document looked highly plausible and the domain was almost correct. Anyone who had tried browsing it would have ended up on the right site.
How Did the Attack Manage to Last for the Whole Four Days?
In his Twitter thread, Sunde specified the following information about the attack. The hacker swiftly altered all links dark.fail to phish passwords, logins and other confidential details. Third-party sites were posing as dark web markets to steal people’s money.
Dark web markets normally accept BTC. Customers transferred their funds to addresses under hackers’ control, believing they were purchasing substances from markets.
Neither Hover nor Njalla could not do anything to stop the crime simply because they were not aware! As soon as they realized what a disaster was going on, they quickly responded to the attack. Yet it took four days to coax Namecheap to transfer the admin rights back.
The Results of the Attack
Now, you can access the fully operational onion version of dark.fail through the Tor browser. Plus, you can find archived versions of dark.fail displaying its dark web market status reports.
The organizers of the attack remain unknown. There is no clear evidence on how many people fell prey to hackers.
And the Trickiest Thing Is That…
Namecheap fails to admit that the court order was forged! The paper looked like it was 100% real. The company even issued a statement to support its point of view. The domain mentioned in the court order is registered through them. The web redirect is hosted with them and the incoming email is hosted by them. It hardly makes sense to deny the facts…
In his Twitter, Sunde repeats how well-versed the hacker is — and his words can serve as a warning for everyone else.
Dark.fail alternative
After the hack, dark.fail owner decided to move all content to https://dark.pe
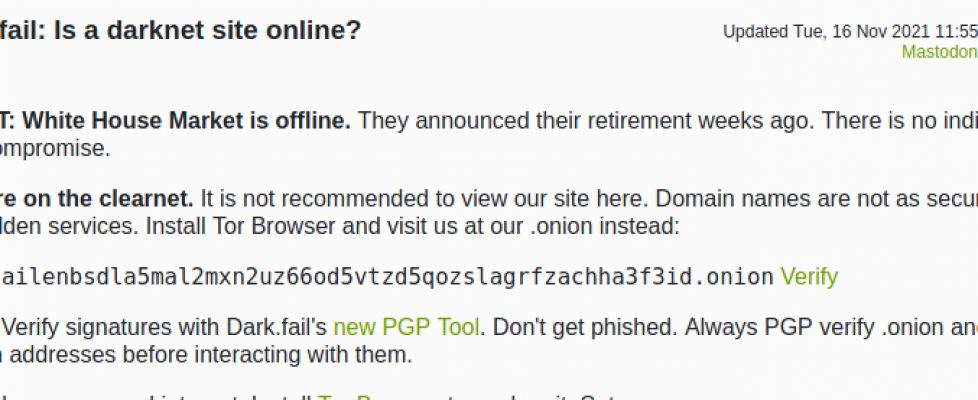



Does “dark.pe” have an onion address?